I want to try it out myself you say.
Here is a video explanation using Kickstarter.com as an example:
And here are the steps you take to verify the weakness yourself–using Kickstarter.com, as well as on other websites you suspect are using Rails’ CookieStore (such as those on this list):
- Install a Chrome plugin such as Edit This Cookie to make viewing and editing cookies easier.
- Go to a site such as Kickstarter.com (no SSL!) or one you suspect is using Rails’ CookieStore.
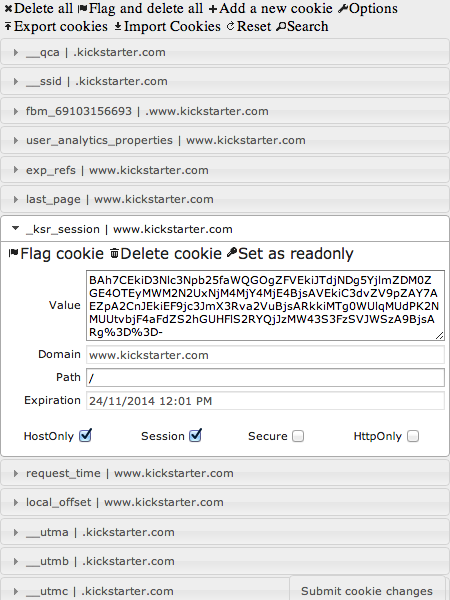
- Find a cookie whose value starts with “BAh7”. That’s a good indicator of Ruby on Rails CookieStore-based websites before version 4.0 of Rails, or those that don’t encrypt their CookieStore values. The session cookie will have a value starting with “BAh7” then a separator of “–” then a hash digest.
- Open Edit This Cookie using the little icon in the top right of your browser. Find the cookie whose value starts with “BAh7” and take note of the cookie’s name. In the case of Kickstarter.com it’s “_ksr_session”. Copy the entire cookie data (“BAh7…”).
- Log out of the website.
- Open Edit This Cookie and overwrite the session cookie’s current value (“_ksr_session” in this case) with the data you copied previously.
- Go to the website. You should be in again!